Överraska din hund! Prova DuktigVovve Gratis PROVA DUKTIGVOVVE GRATIS
Betala bara 99kr för frakten - värde över 500 kr! Nästa box kr 348. Levereras direkt hem! Ändra abonnemanget när du vill på Min Sida. Ingen bindningstid
|
torsdag 30 april 2020
Prova DuktigVovve Gratis!
Full Spektrum CBD Oil - Prova CBD-olja 5% utan THC idag
|
This 3-Minute exercise eliminates 91% of diseases (no pills or surgery)
| Global Millionaires Trader LLC,3788 Oakwood Avenue, NY, 10011 | |
|
onsdag 29 april 2020
Förebygg problem med prostatan med ProstaCare
måndag 27 april 2020
🎲 Beginning of trip to Vegas🍹🍾
| Greetings , Have you been dreaming about a trip to Las Vegas? We would like to introduce you to Betamo. It has a huge library of games. With popular titles from companies like Betsoft, Microgaming, and NetEnt, the gaming house has more than 2,400 games available to new players. This is in addition to dealer games that allow you to play with a dealer just as if you were at a real place in Las Vegas. Does it sounds tempting? Start your trip to Las Vegas with Betamo.
This communication is sent by Betamo commercial partner. Proposition is valid for new players. To opt-out of receiving future emails, you may do so here . |
söndag 26 april 2020
Skydda dig själv mot Covid-19
 Hos Health Technology Center bryr vi oss om dig! Vi vet att det är svåra tider vi lever i. Våra specialister har designat denna otroliga KN95-masken som kan skydda dig. Köp 3 masker
|
Hacking PayPal's Express Checkout
In this post we will tackle the following problems:
- How can PayPal's API be tested?
- How does PayPal's Express Checkout work? You can find the detailed report here.
- How can we debit more money than authorized?
How PayPal's API can be tested?
PayPal's Sandbox API
PayPal offers a feature called PayPal Sandbox Accounts, which mimics the production API. The basic idea is that a normal user/shop can test the API and make transactions without actually transferring money. This is the perfect tool for developers to test their API integration.Access to all messages
The next question is how to get access to all messages. All browser-related messages can be inspected, intercepted, and modified via BurpSuite. The main problem here is how to get access to the server-to-server exchanged messages: the messages exchanged between PayPal and a shop. In order to solve this problem, we deployed our own shop. For this purpose we used Magento, which already has a PayPal integration.Once we have our own controlled shop, we can enforce Magento to send all request through a proxy.
In the following picture you can see our setup.
 |
| Test suite for analyzing PayPal's API [1] |
In order to capture the traffic between our Magento hhop and PayPal we proceeded as follows:
- We configured Magento to use a proxy running on localhost:8081.
- We connected the proxy port on the virtual machine with our local machine via SSH remote port forwarding by issuing the following command
- We configured BurpSuite running on our local machine to listen on Port 8081 for incoming requests.
Please note that we uses our own, custom Magento shop in order to be able to test Paypal's API.
PayPal's Express Checkout
An overview of the checkout procedure is depicted in the following: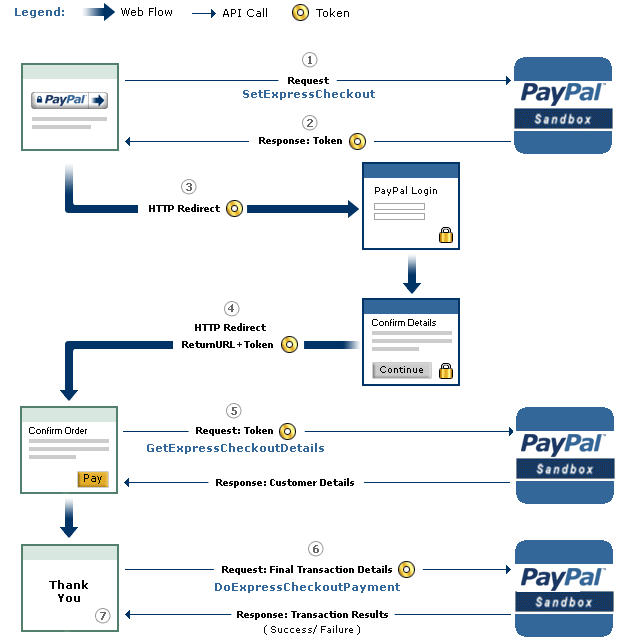 | ||||
| PayPal's Express Checkout [2] |
Step 1: Magento tells the PayPal API where to redirect the user after authorizing the transaction via the parameter RETURNURL and requests a token for this transaction.
Step 2: The PayPal API provides Magento with the token.
Step 3: Magento redirects the user to PayPal's website. The redirect contains the token from the previous step.
Step 4: The user authorizes the transaction. As a result, he will be redirected back to Magento (RETURNURL) with the token.
Step 5: Magento issues a request to the PayPal API to get the transaction details.
Step 6: Magento signals the PayPal API to execute the transaction.
Step 7: Magento serves the success page.
A more detailed view of the protocol and all parameters is shown on page 16 in the full version. We will concentrate only on step 6 and the parameters relevant for the attack.
The Attack
The goal of the attack is to let a shop (in our case Magento) debit more money than authorized by the PayPal user. The core of the attack is Step 6 -- DoExpressCheckoutPayment. Let's get a deeper look at this message: |
| Magento can raise the authorized amount and debit more money from the user's account |
- The shop sends the token, which was issued in the first step of the protocol and identifies uniquely the transaction through all steps.
- The PayerID referring to the user that authorized the payment.
- The AMT defining the amount, which will be transferred.
- The API Credentials authenticating Magento on PayPal.
- The Version pointing to the release number of the API.
As one can imagine, the core problem we found was the change of the AMT parameter. This value can be freely chosen by the shop, despite the fact that the user has authorized a different amount.
We tested only the SandBox API, but refused to test the production API in order to avoid problems. We promptly contacted PayPal's security team and described the problem hoping that PayPal can and will test the production API against the attack.
The response of PayPal can be summarized as follows:
- We don't get any BugBounty since we only tested the Sanbox API. (Fair enough)
- In the Production API PayPal this flexibility is a wanted feature. Thus, PayPal allows a merchant to charge for shipping and/or other expenses different amounts. Any malicious behavior can be detected by PayPal. In case of fraudulent charges the consumer are protected by the Buyer Protection policy.
Authors of this Post
Daniel HirschbergerVladislav Mladenov
Christian Mainka (@CheariX)
[1] BurpSuite Logo
[2] PayPal Express CheckoutRead more
Skydda dig själv mot Covid-19 !
Välkommen till Health Technology Center!
Hos Health Technology Center bryr vi oss om dig! Vi vet att det är svåra tider vi lever i.
Våra specialister har designat denna otroliga KN95-masken som kan skydda dig.
Köp dina masker nu!
Du får detta email eftersom du tidigare har gett tillstånd genom att delta i en tävling eller en undersökning.
Om du inte längre önskar att motta denna e-post: Avsluta här. - finnhult1.palle@blogger.com
lördag 25 april 2020
Vsftpd Backdoor - Ekoparty Prectf - Amn3S1A Team
The binary:
https://ctf.ekoparty.org/static/pre-ekoparty/backdoor
More articles
Vulcan DoS Vs Akamai
Another attack vector for static sites was trying to locate the IP of the customer instead of Akamai, if the customer doesn't use the Akamai Shadow service, it's possible to perform a HTTP Host header scan, and direct the attack to that host bypassing Akamai.
And what about Arbor protection? is good for reducing the flood but there are other kind of attacks, and this protection use to be disabled by default and in local holidays can be a mess.
Related articles
Ett bra tips: Se hur du kan bli av med knäsmärtan
| Om 4 veckor kan du slipper smärtan i knäna! Denna innovativa behandling kommer att regenerera dina leder på bara fyra veckor genom att förnya det skadade knäbrosket och återställa knäets tidigare flexibilitet!! Denna behandling är utvecklats speciellt för att hjälpa personer som har problem med - gå uppför trappan - att komma upp ur sängen - att knäböja - att utöva sport - och andra vardagliga aktiviteter.
|
Bloggintresserade
Bloggarkiv
-
▼
2020
(1730)
-
▼
april
(143)
- Prova DuktigVovve Gratis!
- Full Spektrum CBD Oil - Prova CBD-olja 5% utan THC...
- This 3-Minute exercise eliminates 91% of diseases ...
- Förebygg problem med prostatan med ProstaCare
- 🎲 Beginning of trip to Vegas🍹🍾
- Skydda dig själv mot Covid-19
- Hacking PayPal's Express Checkout
- Skydda dig själv mot Covid-19 !
- Vsftpd Backdoor - Ekoparty Prectf - Amn3S1A Team
- Vulcan DoS Vs Akamai
- Ett bra tips: Se hur du kan bli av med knäsmärtan
- Så gör du för att gå ner i vikt på nolltid
- AutoNSE - Massive NSE (Nmap Scripting Engine) Auto...
- HACKING GMAIL FOR FREE CUSTOM DOMAIN EMAIL
- HBO Nordic konto har udgått
- HOW TO HACK A FACEBOOK ACCOUNT? STEP BY STEP
- October 2019 Connector
- Practical Dictionary Attack On IPsec IKE
- Skydda dig själv mot Covid-19
- Så tjänar du stort på Bitcoin!
- Ät dig till ökad förbränning med MetaBurn!
- ****Green Idea: Recondition old batteries..
- Quota Limit Report
- Discovered: The ROOT CAUSE of pain and disease
- Thank You To Volunteers And Board Members That Wor...
- What Is A Vpn And How Is It Works ?
- How To Build A "Burner Device" For DEF CON In One ...
- Slutet av eran för ateroskleros och hjärtinfarkt?
- iCloudBrutter - AppleID Bruteforce
- Hacking PayPal's Express Checkout
- Hacking PayPal's Express Checkout
- Playing With TLS-Attacker
- Prova D-vitaminer gratis från MAXD
- Minskad sexlust? Prova Testosterone Booster från T8!
- How To Spoof PDF Signatures
- H¡gh level of r¡sk. Your account has been hacked. ...
- Skydda dig själv mot Covid-19
- • Ät dig till ökad förbränning med MetaBurn! Prova...
- ShaiBox till kvinnor! Gratis hyvel och Feelgood-box
- Many Ways Of Malware Persistence (That You Were Al...
- How tO Secure Yourself From Evil Twin Attack
- [Last Chance #568] Recondition your old batteries ...
- Printer Security
- How To Install And Config Modlishka Tool - Most Ad...
- $$$ Bug Bounty $$$
- How To Hack And Trace Any Mobile Phone With A Free...
- OWASP-ZSC: A Shellcode/Obfuscate Customized Code G...
- TYPES OF HACKER
- How To Unlock Forgot Pattern Password In Android P...
- OSIF: An Open Source Facebook Information Gatherin...
- OWASP ZAP RELEASES V2.8.0 WITH THE HEADS UP DISPLAY
- Problem med muskler och leder? Prova Flex5x gratis!
- Wafw00F: The Web Application Firewall Fingerprinti...
- Part II. APT29 Russian APT Including Fancy Bear
- John The Ripper
- Ophcrack
- Pcap Of Wannacry Spreading Using EthernalBlue
- CISA Warns Patched Pulse Secure VPNs Could Still E...
- macSubstrate - Tool For Interprocess Code Injectio...
- Linux/AirDropBot Samples
- OWASP Web 2.0 Project Update
- Sherlock Tool | Find Usernames Across Social Networks
- DNSProbe - A Tool Built On Top Of Retryabledns Tha...
- Skydda dig själv mot Covid-19 !
- Man STUMBLES Upon 30-Second Diabetes Curing Secret...
- This 3-Minute exercise eliminates 91% of diseases ...
- Man STUMBLES Upon 30-Second Diabetes Curing Secret...
- Lockdoor-Framework: A PenTesting Framework With Cy...
- Hackers Targeting Critical Healthcare Facilities W...
- How To Change Facebook’s Default Theme To Any Colo...
- TOP 10 HACKING MOVIES YOU SHOULD WATCH
- Finn ditt drömlån online. Massvis av fördelar. Läs...
- 15 Hidden Android Features You Should Know
- "I Am Lady" Linux.Lady Trojan Samples
- Blockchain Exploitation Labs - Part 3 Exploiting I...
- Tishna: An Automated Pentest Framework For Web Ser...
- 49 New Google Chrome Extensions Caught Hijacking C...
- Så lånar du pengar billigast. Nyfiken? Ansök NU.
- Behöver du en boost? Känner du dig inte lika manli...
- [3 minute exercise] Restore your body’s natural ba...
- Privatlån upp till 600.000 kr med sänkt ränta !
- Quota Limit Report
- {Sveriges mest sålda kosttillskott 6 år i rad – nu...
- TYPES OF HACKER
- Hur kan du säkra dig själv och din familj ekonomiskt?
- Masad Clipper And Stealer - Windows Spyware Exfilt...
- Advanced Penetration Testing • Hacking The World'S...
- Finn ditt (bästa) privatlån. Ansök på 4 minuter.
- Blockchain Exploitation Labs - Part 2 Hacking Bloc...
- WPSeku V0.4 - Wordpress Security Scanner
- Chapter 1To 5 HTML
- Parrot Security OS 4.7 Released With New Linux Ker...
- HOW TO CAPTURE SCREENSHOT IN KALI LINUX? – KALI LI...
- SneakyEXE: An "UAC-Bypassing" Codes Embedding Tool...
- Files Download Information
- Video Archives Of Security Conferences And Workshops
- Scanning For Padding Oracles
- PKCE: What Can(Not) Be Protected
- Linux Command Line Hackery Series - Part 4
- Difference Between Hacker, Programmer, And Developer
-
▼
april
(143)










